Security Operations Centers (SOCs) play a vital role in safeguarding a company's IT environment and preventing cyber incidents. In this blog post, we will explore the functions of a SOC, why it is essential for businesses, the challenges they face, and how to set up an effective SOC.

What is a SOC?
A SOC is a dedicated unit responsible for real-time monitoring, incident detection, and response in an organization's IT infrastructure. SOC experts collect and analyze data from various sources to identify and mitigate potential cyber threats. Their key functions include:
- Active Monitoring and Incident Data Collection: SOC operators continuously monitor the IT environment, collecting information from workstations, network devices, and other infrastructure objects. This proactive approach helps in early detection of potential attacks.
- Analysis of Suspicious Events: When alerted about a potential incident, SOC experts analyze the nature and severity of the threat to assess the level of risk and devise appropriate response strategies.
- Threat Response: In the event of a cyber incident, SOC employees take immediate actions to eliminate the threat and minimize any damage. This involves coordination with other teams to implement necessary security measures.
- Post-Incident Recovery: SOC experts play a crucial role in the recovery phase, ensuring damaged systems are restored, files are recovered from backups, and any residual effects of the incident are addressed.
- Incident Investigation: SOC teams participate in thorough investigations to identify the causes of cyber incidents. The insights gained from these investigations help organizations prevent similar incidents in the future.
- Resource Register Maintenance: Maintaining an up-to-date register of company resources is vital for SOC operations. This includes keeping track of infrastructure objects and the information security products used to protect them.
- Compliance Management: SOC employees are responsible for ensuring corporate data security and often handle compliance with relevant data security regulations such as GDPR, HIPAA, and CPPA.
Why Set Up a SOC?
Establishing a SOC provides several benefits, including:
- Proactive Threat Detection: SOC teams actively monitor the IT environment, enabling early detection of potential cyber threats.
- Rapid Incident Response: With a dedicated SOC, organizations can respond quickly and effectively to cyber incidents, minimizing the impact and reducing recovery time.
- Enhanced Cybersecurity Posture: A SOC strengthens overall cybersecurity by continuously monitoring, analyzing, and improving security measures.
- Regulatory Compliance: SOC teams help organizations meet data security regulations and maintain compliance with industry standards.
Setting Up a SOC:
When establishing a SOC, there are several approaches to consider:
In-House SOC: Create a dedicated team within your organization responsible for SOC functions. This team can be composed of internal experts with cybersecurity knowledge and training.
Cross-Departmental SOC: Combine SOC responsibilities with existing IT or security teams, leveraging their expertise to enhance the overall security posture of the organization.
Outsourced SOC: Engage a specialized company that provides remote infosec monitoring and response services. This option allows you to benefit from the expertise of experienced professionals without the need for significant internal infrastructure investment.
Conclusion: Security Operations Centers are vital in maintaining a robust cybersecurity posture for organizations. By understanding their functions, benefits, and challenges, businesses can establish an effective SOC that proactively detects and responds to cyber threats.
Remember, protecting your organization starts with a proactive approach and a strong SOC.
Stay secure with related Kaspersky Solutions!
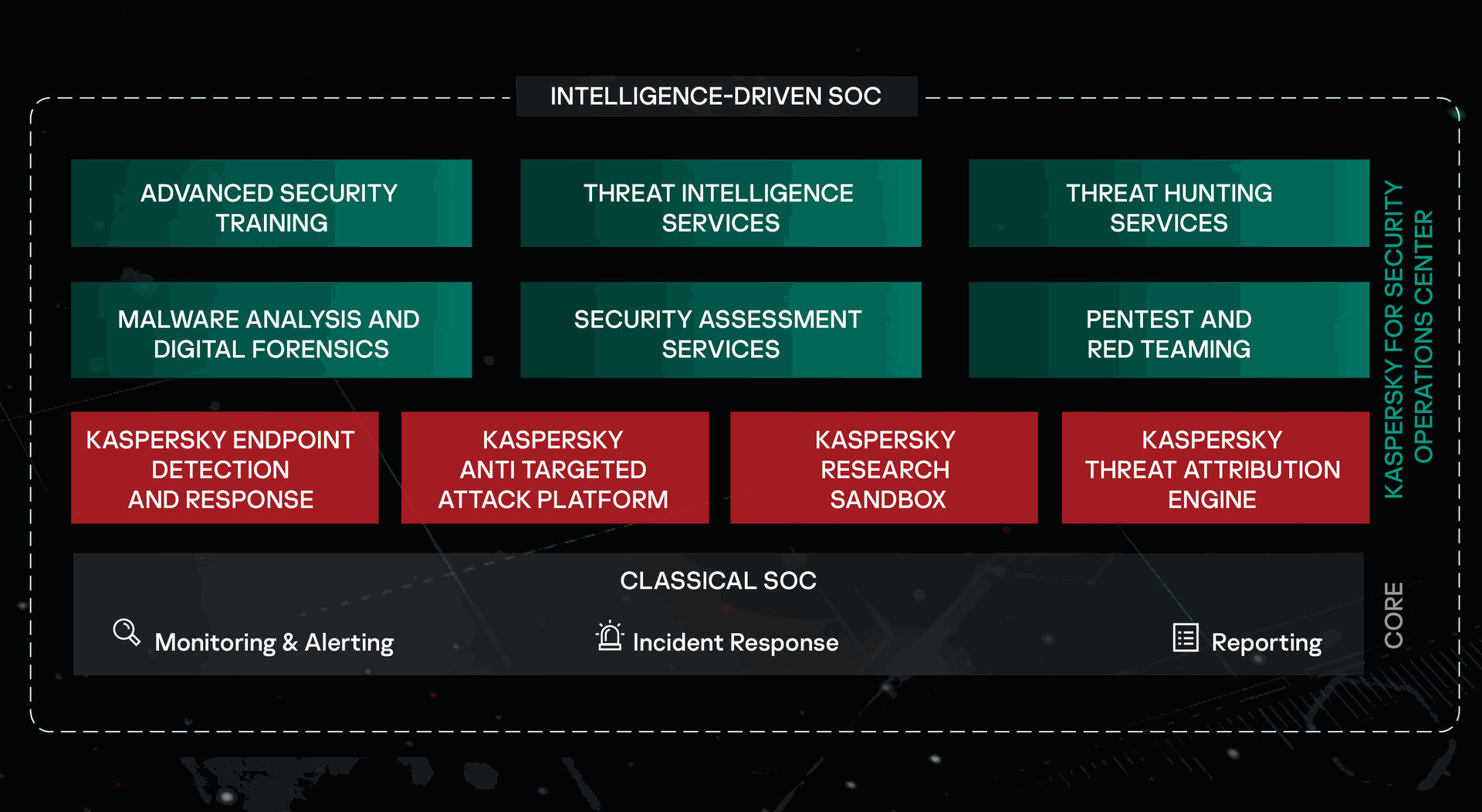
To fight modern global cyber threats, it's not enough to just build a Security Operations Center (SOC) in the conventional sense – you need a SOC that is equipped with the technologies, security intelligence, and knowledge that empowers it to adapt to ongoing challenges in a changing threat environment. With over two decades of constant threat research, leading protection technologies recognized expertise, and proven experience in complex cybersecurity projects, Kaspersky powers your SOC at every level for greater efficiency in fighting increasingly sophisticated threats.
Contact us today if you are looking for a reliable SOC provider in Nepal.
